
Is your company safe from data breaches?
Nowadays, businesses generate a large volume of information. The increase in the number of data that a company manages is exponential throughout its life cycle, which makes its treatment and storage difficult. So much so, that many entities find themselves ...
A Deep look into the SAP-C01 Exam Status and value in IT industry and way to crack it with high score
It is considered a challenging task in the industry to get certified with this certification. But SAP-C01 AWS Certified Solutions Architect - Professional has turned it into an easy task by providing the candidates with precise and concise exam material. ...

Cognitive cloud computing for video content analysis
Video content is now more popular than ever.
A lot of different businesses found all kinds of use for it: training, marketing, education, entertainment, and so on.
And as it seems, the people appreciate the format: digital video viewership continues to grow ...

5 Changes to SAN Storage In 2026
A dedicated network of storage devices used to be everything in computing. Commonly known as storage area networks or SAN, these units solely provide shared storage for multiple servers and computers.
SAN came with increased performance, availability, centralized management, scalability, and ...

Cybersecurity Fintech Trends for 2026
Fintech companies face a particular set of challenges when it comes to cybersecurity.
Fintech organizations acquire personally identifiable information ("PII") and other sensitive data from their clients on a regular basis. If a Fintech company fails to protect this PII or ...

Introduction to the SAA-C02 (AWS Certified Solutions Architect Associate) certification
Take your newly developed and highly demanding IT career to the next progressive level by earning your AWS Certified Solutions Architect Associate certification. During this course, you will have a comprehensive understanding of the components that form the Well-Architected Framework ...

ETL VS ELT: The Key Differences
In this article, we will explore the topic of ETL (Extract, Transform, Load) and ELT (Extract, Load, Transform) to avoid confusion between these two data integration methods. Both of them have advantages as well as downsides. Which type to choose ...

How to Protect Your Company from Internal Cybersecurity Threats
A barrage of cyberattacks is raining down on businesses of all types and sizes. Every day in the U.S., there are about 2,200 cyberattacks. This crumbles down to about 39 per second!
As a business owner, you’re obviously worried about cybersecurity. ...

Sizing Up The Intangible Face Of Modern Cyber Attacks
High value intelligence targets are facing a myriad of cyber threats - at an unprecedented scale. What’s more, according to Wired, it’s difficult to tell exactly where those threats are coming from and what they will target. The threat is, ...
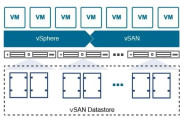
The Benefits of Using vSAN over RDMA
VMware vSAN-based HCI solution (Source: VMware)
You might want to run vSAN over RDMA to boost the performance of your IT infrastructure. Read this article to get to know about the main advantages of this approach!
Accelerated computing has become one of ...






















