
10 Ways To Transform IT Management At Your Business
Ready to revolutionize your business's IT management? Let's dive into ten game-changing strategies that will boost efficiency, save time, and make your life a whole lot easier.
1. Windows App Publishing via Third Party
First up, let’s talk about Windows app publishing. ...

Boost Your App Performance: Choosing the Right CDN Provider
According to statistics, 88% of customers are less likely to come back once they have a bad user experience, and in the present digital world, where UX matters, and in some cases determines whether an app will succeed or not, ...

Spreadsheets, Databases, & Hybrid Solutions
IT admins and tech-savvy professionals at fast growing organizations often face a fork in the proverbial data management path: selecting the right tools that blend ease of use, scalability, and robust functionality. Traditionally, the choice has boiled down to using ...

Challenges in Data Quality Management and How to Overcome Them
Quality management of data is a crucial pillar supporting effective decision-making and operational efficiency. Data reliability, accuracy, and consistency directly impact organizational success. However, ensuring high data quality is not without its hurdles. So, explores five prevalent challenges in data ...

The Essential Guide to Penetration Testing for Enhanced Cybersecurity
In today's digital age, where businesses operate increasingly online, cybersecurity has transitioned from a nice-to-have to an absolute necessity. The stakes are particularly high for small business owners and IT professionals, who must protect not only their own data but ...

Build Scalable Data Pipelines: Proven Best Practices for Snowflake
Data engineering drives today's digital transformation efforts, enabling businesses to increase efficiency, innovation, and profitability in the data-driven era. Snowflake is a leading data platform that offers a comprehensive suite of services that revolutionize how organizations utilize data. Its services ...

Strategies to Combat Zero-Day Vulnerabilities
When discussing cybersecurity threats, any member of the general public could probably name several of the most common forms, like phishing, malware, and ransomware. Far fewer know about zero-day vulnerabilities, which are a form of attack that flies under the ...
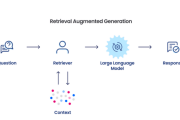
The Power and Challenges of Unstructured Data in Relation to Retrieval-Augmented Generation
Unstructured data, encompassing formats such as text, images, audio, and video, makes up a majority of the data available in the digital age, often lacking a predefined data model or not easily fitting into relational tables.
As businesses and entities attempt ...

10 Best VPS Hosting in 2024 – Ultimate Suggestions
Are you tired of shared hosting limitations and ready to take your online presence to the next level? Look no further than Virtual Private Server (VPS) hosting! With VPS hosting, you get the flexibility and control of a dedicated server ...

How Tour Operator Software Can Improve Your Travel Business
How Tour Operator Software Transforms Your Travel Business Enduringly
In the age of technology disrupting industries continually, digitally progressive travel companies consistently outperform laggard peers clinging onto legacy approaches firmly. Tour operators, in particular, face intensifying online competition from OTAs and ...




















