
List of Web Components for Building an Analytics Dashboard
Dashboard is an effective way to visualize data due to their clarity, conciseness, and user-friendly interface. They are widely used to track key performance indicators (KPIs), analyze trends, and help to gain compelling insights and make informed decisions. There are ...

60% Of UK Businesses Choose Outsourcing: Why Cyber Security is on the List
In an era where data breaches and cyber threats loom large, businesses face an increasing challenge to secure their digital assets. A growing trend in response to this challenge is the outsourcing of cyber security procedures. According to studies, approximately ...

10 Trends of Business Intelligence to Facilitate Data Analytics and Decision Making
As the volume and complexity of data continue to surge, the way businesses access, analyze, and act upon their data are reshaping. In this article, we delve into the top 10 trends in Business Intelligence that enrich data analytics and ...

The Future of Quantum Computing and Its Implications
Hi, Tech Enthusiast! Picture this: a powerful computer makes our machines look like ancient abacuses. Sounds like something out of a sci-fi movie, right? But, believe it or not, that’s the trajectory we’re on with quantum computing. Dive in with ...

10 Ways in which Cloud & AI Can Boost Integrated Logistics
The logistics landscape has evolved dramatically in the past decade, thanks partly to groundbreaking Artificial Intelligence (AI) development and Cloud Computing. These innovations are not just changing how we understand logistics; they are redefining the gold standards for efficiency, reliability, ...

Driving Efficiency and Profits with Car Rental and Leasing Software
The purchase and maintenance of one's own car often come at a considerable cost, which is why exploring affordable options for car finance in Australia can be a prudent choice. This issue is frequently encountered by residents of major cities ...
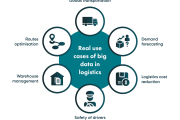
Reducing Costs and Waste: The Role of Big Data Analytics in Logistics Industry
Utilizing analytics is critical to guarantee the proper operation of supply chains and services in the globalized and interconnected society we live in today. The use of big data for logistics and supply chain management has become an important game ...

How to Find an AWS Migration Partner
Migrating to AWS is a very complex process, so finding the right partner to help guide the process is important. Below are some key points to consider in your search.
In the event that you are searching for a Relocation Accomplice ...
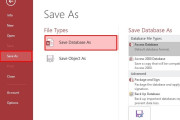
How to Fix Corrupt MDB File and Recover Data?
A corrupted MDB file can lead to multiple errors in Access. Read this comprehensive guide to learn the causes behind MDB file corruption and some effective methods to fix the corrupt MDB file and recover the data. It also mentions ...

UK Cloud Backup and Recovery Services Provided by Experts
Most businesses and organizations in the UK and other parts of the world run on data as the lifeblood in this digital era. This is also the case with individuals who want to stay focused and informed in life. Losing ...






















