
What Is Data Privacy and Why Is It Important for Businesses?
Data is the lifeblood of any organization. From invoices to email correspondence, all this data contains pertinent details that need to be protected to keep your organization afloat in the current era. Having this information fall into the wrong hands ...
How Rotating Residential Proxies Make is Web Scraping Efficient?
Someone might desire to scrape a website for various reasons, such as market research, data analysis, data collection, or just because the data would not be readily available in another way. No matter the motivation, if you want to start ...

How To Manage Endpoint Security
Due to the COVID-19 pandemic, the vast majority of businesses had to shift their on-premise work models to work-from-home models. In 2020, remote work models burst into our lives because of global lockdowns and curfews, but within two years, remote ...

Cloud Vulnerability Management: What It Is, Features, Vulnerabilities, and More
Cloud Vulnerability Management is about finding, judging and improving security risks in systems that use cloud technology. It is important to have a robust Cloud Vulnerability Management program in place to protect your organization's data and systems. In this article, ...

Best Tech Tips To Enhance The Export Potential Of Your Business
International trade has fewer barriers after the globalization of the major economies. Not surprisingly, more and more business owners are keen to explore the domain, regardless of its size and scale. But the idea of foraying into exports may seem ...

How to Ensure Secure and Complete Data Destruction
When decommissioning computers, it is essential to ensure that all data is deleted completely. This can include overwriting, encryption, and shredding. Regardless of the type of data destruction, the process should include a clear audit trail and sanitization certificates.
Overwriting
Overwriting data ...

The Pros And Cons Of Managed IT Services
Information technology (IT) has grown to the point that it underpins most business processes through automation, artificial intelligence (AI), and other IT solutions.
Businesses invest in IT for various reasons. One reason is that it improves efficiency. IT is also a ...

Tentacle Information Security Is Best For You
Thinking About Staying Safe Online
There is an indelible link between internet safety (https://computer.howstuffworks.com/computer-internet-security-channel.htm) and project management, specifically because communication is one of the most easily pregnable areas of a business’s security. People do not realize that many of the ways ...
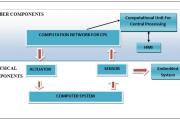
Cyber Physical Systems: features, Applications and Challenges
Cyber-physical systems (CPSs) are smart systems that depend on the synergy of cyber and physical components. They link the physical world (e.g. through sensors, actuators, robotics, and embedded systems) with the virtual world of information processing. Applications of CPS have ...

A Comprehensive Guide to Microsoft 365 Security & Compliance Center
With cybercrime on the rise, it's more important than ever to ensure your business is protected. But is it true that Microsoft 365 security and compliance center can help you and your organization in many ways? If you want to ...






















