
Automated Hiring Software: Why Businesses Use It
Automated hiring software is a tool that streamlines recruitment by automating tasks like job postings, resume screening, interview scheduling, and candidate communication. It reduces the workload for recruiters while improving the hiring experience for applicants.
Businesses use automated hiring software to:
Reach ...

Building a Unified Data Management Strategy with Lineage Integration
In today's data-driven world, databases play a crucial role in storing, managing, and retrieving vast amounts of information. As organizations continue to generate and rely on data for decision-making, the need for a robust data management strategy becomes increasingly important. ...
Gigasheet’s Innovative Solution for Healthcare Price Transparency Data
Gigasheet, the leading self-service analytics platform, is transforming how businesses, researchers, and policymakers analyze healthcare price transparency data by making massive machine-readable files (MRFs) accessible to all.
With growing regulatory requirements mandating that insurers and providers publish negotiated rates and pricing ...

Why is a German VPS the best choice for traders and gamers?
Virtual Private Servers (VPS) have become an indispensable tool for many users, especially traders and gamers. However, among the various options, the German VPS stands out as one of the best choices for numerous reasons. In this article, we will ...

Best Cyber Forensics Software in 2026: Top Tools for Windows Forensics and Beyond
In the ever-evolving world of cybersecurity, cyber forensics software has become indispensable for investigating digital crimes, recovering lost data, and analyzing cyber threats. As we step into 2026, the demand for advanced forensic tools has skyrocketed. Windows forensics is no ...

The Role of Databases in Modern Data Management
In today's digital age, databases play a pivotal role in the management and organization of data. As businesses and organizations increasingly rely on data-driven decision-making, the need for efficient and reliable data storage solutions has never been more critical. Databases ...

5 Cloud Marketing Trends Reshaping Our World in 2026
Cloud computing is a transformational force in IT, driving success in a digital-first world. Businesses utilize the cloud for critical functions from large-scale data storage and analytics to delivering web-based services and scaling infrastructure. Most importantly, for disaster recovery purposes, ...
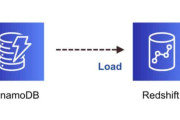
DynamoDB to Redshift: A Comprehensive Guide to Data Migration
Are you looking to analyze large datasets stored in DynamoDB with the advanced capabilities of Amazon Redshift? Moving data between these platforms can unlock powerful insights, making it easier to perform complex queries, generate reports, and leverage Redshift’s analytics prowess. ...

Automation with Windows VPS Hosting
Have you ever found yourself drowning in a sea of tasks, feeling like you’re barely keeping your head above water? I know I have. Picture this: I'm sitting at my desk, coffee in one hand, a keyboard in the other, ...

5 Privacy Threats That Are New to the Business World
In today’s digital age, businesses face a wide range of privacy threats that weren’t even on the radar just a few years ago. As technology advances, so do the methods used by cybercriminals to infiltrate companies and compromise sensitive information. ...



















